Self-custody of Bitcoin represents a fundamental approach for those who wish to maintain full control over their digital assets, allowing users to directly manage their private keys without relying on third parties such as exchanges or custodial wallets.
This approach enhances security by reducing risks associated with centralized platforms while promoting privacy and financial independence.
However, this freedom comes with significant responsibilities that must be carefully considered. Security falls entirely on the user, which requires constant vigilance and a thorough understanding of potential threats.
Here a complete self-custody security framework!
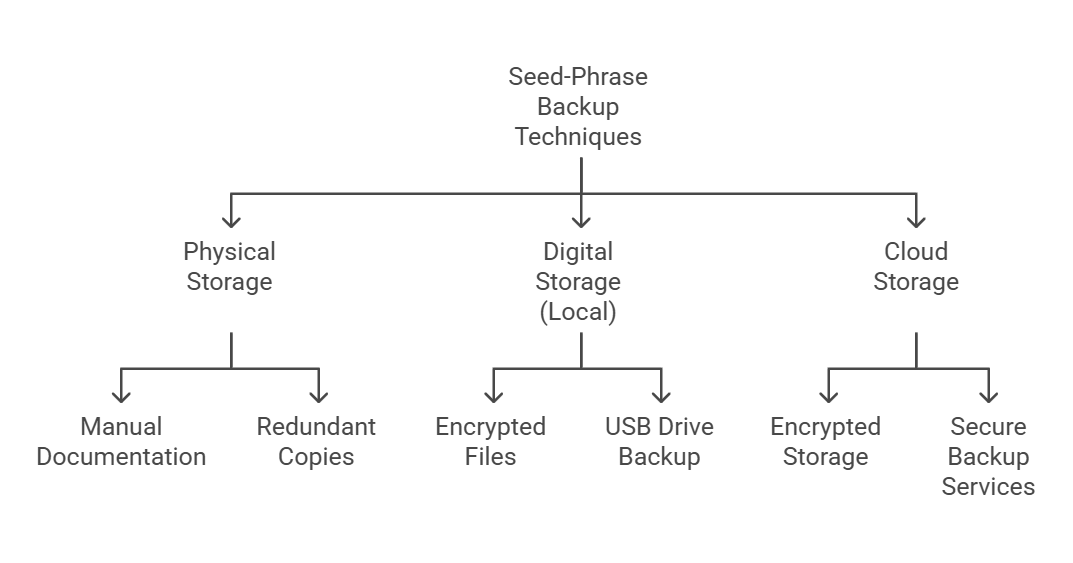
Seed-Phrase Backup Techniques
1. Physical Storage
· Manual documentation: Write down the seed phrase on durable paper or metal plates and store in a secure location.
· Redundant Copies: Create multiple copies of the seed phrase and store them in different locations to ensure access in case of loss or damage.
2. Digital Storage (Local)
· Encrypted Files: Store the seed phrase in an encrypted digital file on a local device using strong encryption software.
· USB Drive Backup: Save the seed phrase on an encrypted USB drive and store it in a secure location, separate from the main computer.
3. Cloud Storage (Advanced Users Only)
· Encrypted Storage: If using cloud services, encrypt the seed phrase before uploading using robust encryption methods. Use services that offer end-to-end encryption.
· Secure Backup Services: Consider specialized security-focused cloud services, but thoroughly verify their security and privacy policies before uploading sensitive information.
Note: Each storage method presents its own security trade-offs. Consider implementing multiple backup methods while prioritizing physical security and encryption at every step.
Security Risks Associated with Self-Custody
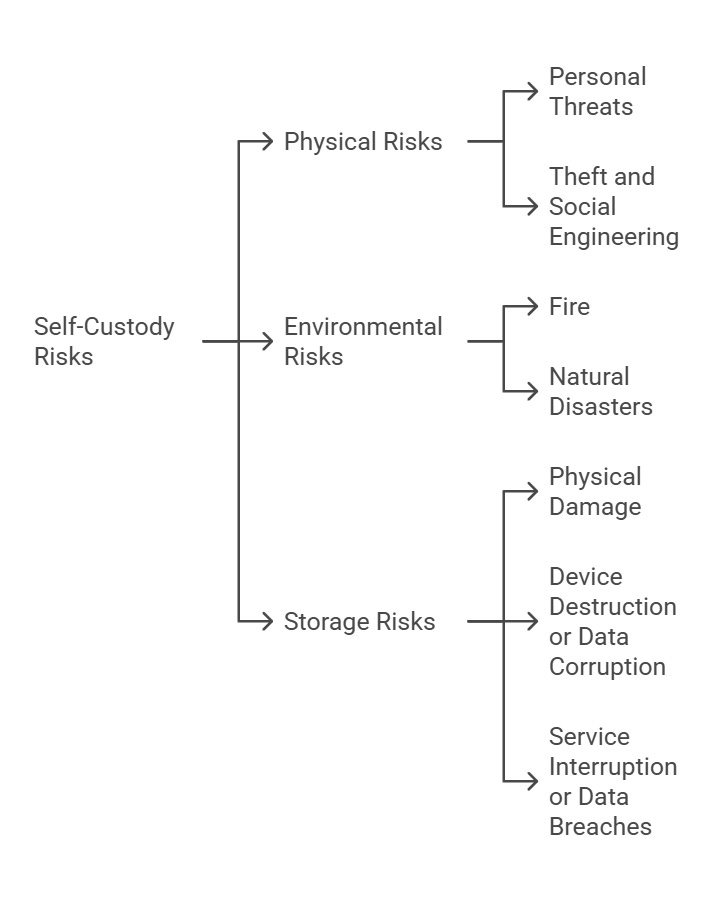
It is essential to analyze the various types of risks associated with self-custody, which can be categorized as physical risks, environmental risks, and digital storage risks.
Each category presents unique challenges that can compromise fund security. Understanding these risks is essential for implementing effective preventive measures and ensuring the protection of assets in the cryptocurrency world.
1. Physical Risks
Physical risks in cryptocurrency self-custody include direct threats to personal security and assets. Among these:
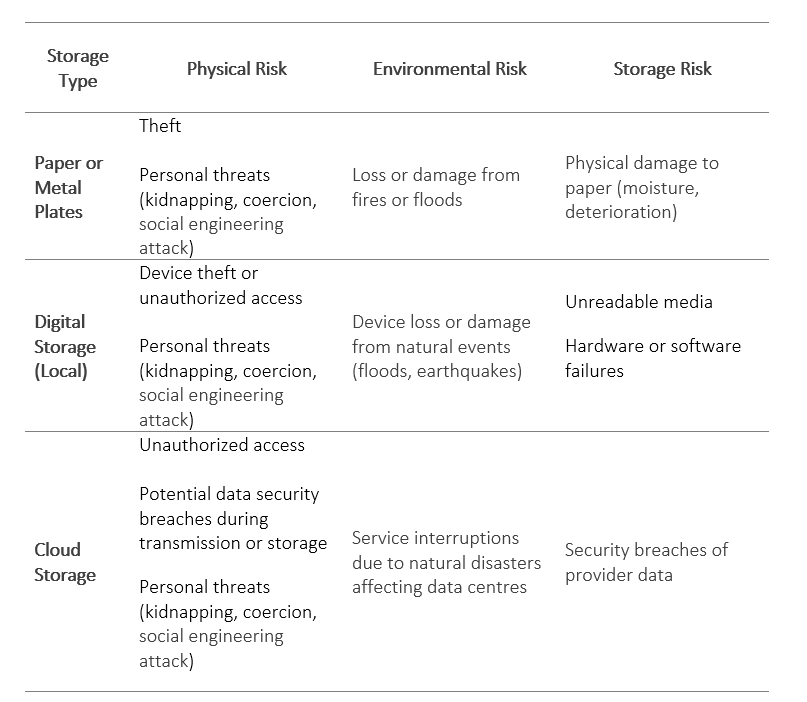
· Personal Threats: Users may be exposed to physical threats, such as assault or kidnapping, by malicious actors seeking access to funds. This situation could force users to reveal their private keys or seed phrases under coercion.
· Theft and Social Engineering: Physical theft of devices containing private keys or seed phrase documentation is a real risk. Thieves may target hardware wallets or backups, especially if they know the user holds cryptocurrencies. Additionally, social engineering attacks can be dangerous, relying on manipulating family members by using gathered information to impersonate others or exploiting basic human empathy to gain access to funds.
2. Environmental Risks
Natural disasters and environmental events can severely compromise the security of backups and devices:
· Fire: A fire can destroy paper backups and digital devices, making fund access impossible if there are no secure copies in other locations.
· Natural Disasters: Events such as floods or earthquakes can damage structures and devices, leading to total data loss if adequate protection measures have not been taken.
3. Storage Risks
Digital storage is vulnerable to various types of failures and problems:
· Physical Damage: Paper can suffer time deterioration. Metal plates are an excellent alternative to paper backups for storing seed phrases, as they offer greater durability over time.
· Device Destruction or Data Corruption: Device failure or breakdown containing digital backups can result in loss of funds if there are no alternative copies. It is crucial to perform regular backups and maintain copies in different formats and locations.
· Service interruption or data breaches (Cloud): Service interruptions due to natural disasters affecting data centres or security breaches can compromise backups and can result in loss of funds.
Security Solutions for Bitcoin Self-Custody
Self-custody of cryptocurrencies offers numerous advantages but also requires careful security management to protect private keys and funds. A single security breach could result in permanent loss of assets, as cryptocurrency transactions are irreversible.
Since it is impossible to completely eliminate risk, alternative solutions must be implemented to reduce and mitigate it.
Here are some solutions to implement based on your level of knowledge and desired trade-offs:
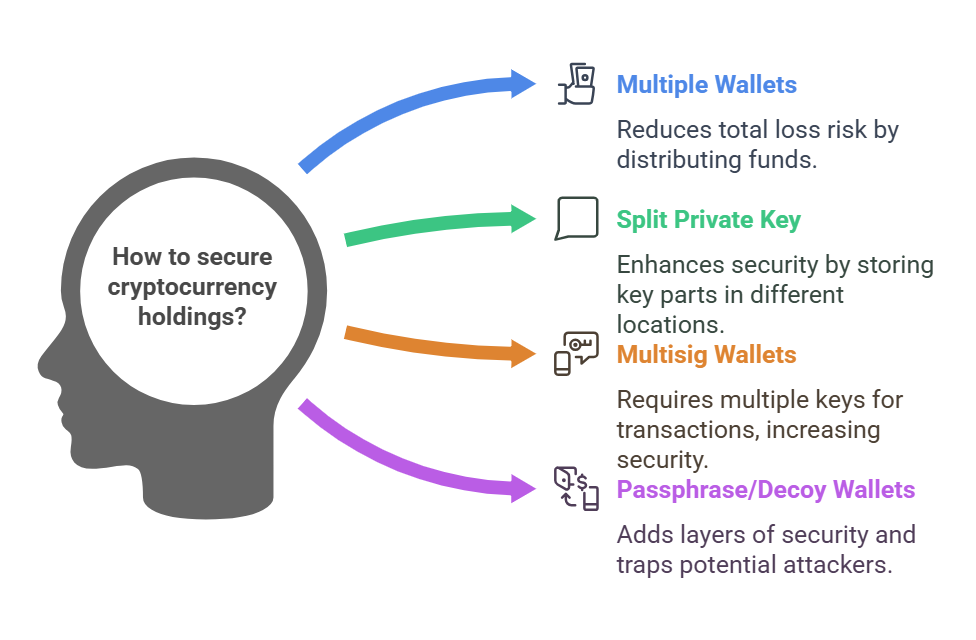
1. Create Multiple Wallets to Divide Crypto
An effective strategy is to distribute cryptocurrencies across multiple wallets. This approach reduces the risk of total loss if one wallet is compromised. For example, you can use one wallet for long-term cryptocurrency holdings (“cold storage”) and another for daily transactions, keeping only a limited amount of funds in the more accessible wallet.
2. Split the Private Key and Save it in Geographically Different Locations
This practice involves dividing the private key into segments, each stored in a separate secure location. Some wallets allow splitting a seed phrase using XOR for added security. Key parts can be stored in different safety deposit boxes, trusted friends’ homes, or separate locations. It’s crucial to ensure future access to all necessary parts to reconstruct the key to avoid losing funds.
3. Use Multisig Wallets
Multisig (multisignature) wallets require multiple private keys to authorize a transaction, thus increasing security. For example, a 2-of-3 multisig setup requires any two out of three designated keys to approve transactions. This solution is particularly useful for businesses or users who want to involve multiple people in fund management, as it reduces the risk of unauthorized access.
4. Use Passphrase or Decoy Wallets
Adding a passphrase to private keys provides an additional layer of security by creating a completely different wallet from the one generated by the original seed. Additionally, using decoy wallets (“honeypot” wallets) can help protect real funds; these wallets contain a limited amount of cryptocurrency and can serve as a trap for potential malicious actors.
5. Save an Altered or Encoded Seed
A DIY technique involves saving an altered or encoded seed or passphrase. This method makes the private key unreadable if discovered and unusable for malicious actors, increasing overall security. Naturally, you must remember the decoding method to avoid losing funds.
Awareness and preparation are fundamental in the cryptocurrency space, where security responsibility falls entirely on you.